Real Server Security for everyone
The Invisible Shield Security protects your website at every level
Invisible Shield Security at every level for your website, data and email
RedyHost integrates the strongest Server Security System from Atomicorp, that works by combining security at all layers, from the applications all the way down to the kernel to provide the most complete multi-spectrum protection solution available for web hosting industry today. It helps to ensure that your website and data are secure and compliant with commercial and government security standards.
The immediate solution for security challenges
While you explore CMS patching options, the WAF and HIPS will protect your website

Atomic Secure Linux brings the best in the web-hosting industry Server Security System (ASL). It provides an immediate solution for security challenges, including the following:
- PCI-DSS compliance
- Self Healing
- Data Theft
- Site Defacement and comment spam
- Web Application Vulnerabilities
- Regulatory Compliance
- Rootkits and Malware
- SQL injection and Cross Site Scripting attacks
- Cookie and Credential Theft
- Advanced Persistent Threats
Zero-day protection
Unlike other security products, ASL (the Server Security System) does not depend on signatures that require constant updating as it includes technology to detect and stop entire classes of attacks such as buffer overflows, SQL injection, cross-site scripting and more!

Invisible Shield Security protects against
Attacks and vulnerabilities mitigation
- DoS Mitigation
- Web Application Firewall
- Intelligent attack blocking and unblocking
- SQL Injection Protection
- XSS Attack Protection
- Daily malware/virus scans
- Daily vulnerability scans
Security system blocked spam comment attempt to a WordPress site
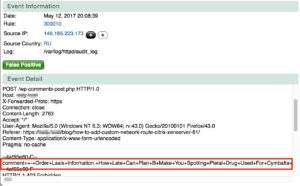
Malware Script Blacklist: Known Malware detected in Request Filename
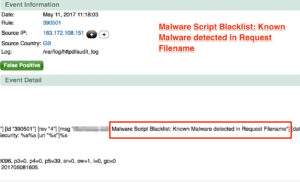
Malware & brute force attacks protection
- Uploads scanner
- Rootkits Protection
- Dictionary Attack Protection
- Brute force protection
- Spam form submission prevention
- Redundant Firewall protection
More Features of the Security System
- Complete Intrusion Prevention: Everything you need to protect your server!
- HIPS: Host Intrusion Prevention System, with built-in rootkit detection and prevention.
- KIPS: Kernel Intrusion Prevention System, prevents insertion of rootkits and malware into the kernel, protects against memory and stack-based attacks and other methods rootkits use to take over your system, Role Based and Mandatory Access Control, Trusted Path and more!
- WIPS/WAF: Web Intrusion Prevention System/Web Application Firewall: Application layer firewalling through mod_security using the industry leading rules and optimised for the web hosting environments. A must for PCI-DSS compliance! Protects against cross-site scripting, SQL injection, remote code inclusion, directory recursion and many many other web-based attacks.
- Realtime shunning/firewalling and blocking of attack sources and user control over automatic "deshunning" timelines.
- Real-time Blacklists of spammers, malware and attackers.
- Full RBL support works with all DNS based RBLs such as Spamhaus and others.
- Geoblocking based on countries.
- Automatic Self Healing System - Not only will RedyHost Server Security System (SSS) protect your system, but it will also automatically fix problems on the system as they occur. From crashed processes to broken applications and system errors, you name it! RedyHost Server Security System (SSS) intelligently analyses the systems logs and condition, and will take action to repair errors, fix misconfigurations, protect processes and so much more. And the Self Healing system is flexible too, using an XML-based system to allow you to easily create your own self-healing rules.
- "Just in Time" Virtual Patching for web applications. Helps to protect vulnerable applications that can not be patched immediately.
- Automated file upload scanning protection, real-time prevention of malicious file uploads such as rootkits, viruses, worms, shells, spambots and more!. Scans all Web, FTP and SSH-based file uploads. Files can be quarantined for further investigation, or can be automatically deleted before they are ever uploaded to the system!
- Built in vulnerability and compliance scanner and remediation system to ensure that your system is operating in a safe, secure and compliant manner.
- Web comment/blog/referrer spam protection.
- Denial of Service protection
- Malware/Antivirus protection.
- Real-time malware/virus/trojan protection from web, file and local based attacks.
- Real Time malware removal system, helps protect a system from accidentally serving up malware.
- Includes Real Time malware, antivirus and rootkit signatures.
- Third party signatures such as Google Blacklists, SaneSecurity, SecuriteInfo and MalwarePatrol.
- Auto-learning Role Based Access Control. Easier to use than SELinux!
- An intelligent and highly secure robust Role-Based Access Control (RBAC) system that can generate least privilege policies for your entire system with no configuration, from the Grsecurity project.
- Auto-learning mode - allows you to generate your own top down least privilege policies.
- We also support SELinux policies.
- Data Loss Protection and Real-time web content reduction system, prevent data leakage of information, such as credit cards, SSNs or other sensitive customer data.
- Automated secure log management with secure remote logging, intelligent log reduction, event detection and alerting! Ships with a world class set of policies that requires no tuning or configuration and works out of the box to detect intrusions, policy violations and system emergencies.
- Real-time e-mail notifications of attacks and system emergencies.
- GUI management of alerting rules and per domain controls.
- Intelligent log reduction and event detection.
- Event correlation.
- Easy to use XML-based policies for custom event detection and alerting.
- Kernel Protection: The Most secure kernel available for Linux, including state of the art stack and heap overflow protection using the PaX and grsecurity projects security enhancements for the Linux kernel.
- More powerful than the execshield and randomization protection found in normal Linux kernels.
- Protects your Linux server against entire classes of exploits in services on the system, such as apache, MySQL, Postgres, bind, secure shell and others.
- Trusted Path Execution, which restricts untrusted users such as apache to execute only trusted applications and commands thus simply preventing a whole class of exploit techniques used by attackers, or internet worms. This can also be used to automatically prevent your users from executing and even uploading dangerous software to your servers!
- Auto Healing/Hardening: Automatically hardens Linux servers based on security policies, and ships with a world class set of policies developed by our security experts.
- Automatically disables unsafe functions in web technologies such as PHP to help prevent entire classes of vulnerabilities.
- Specially hardened chroot capabilities, and protection against exploitable null-pointer dereference bugs in the kernel and other enhancements from the Grsecurity project.
- Users are restricted to only view their processes.
- Sensitive kernel functions are denied to normal users.